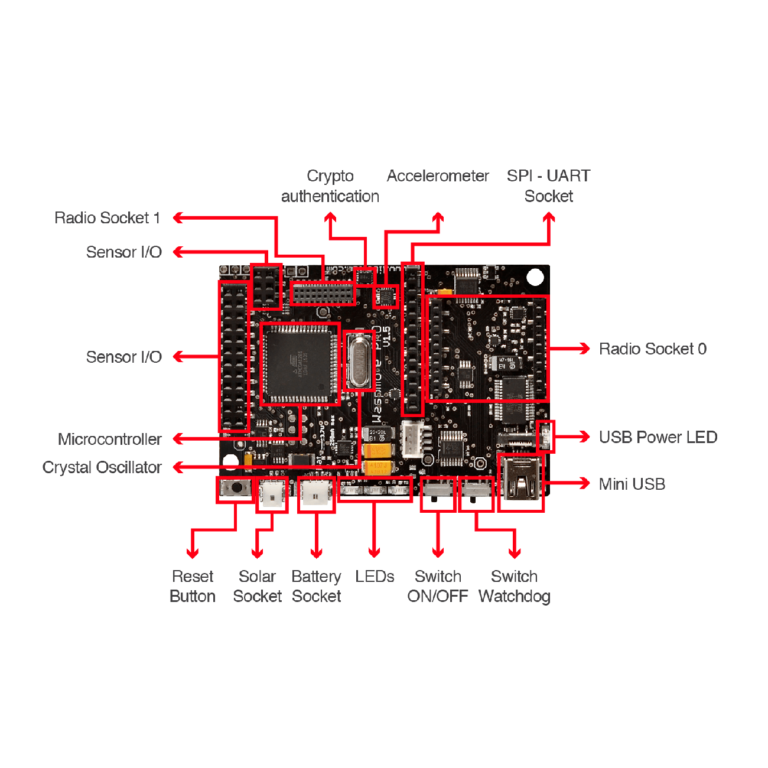
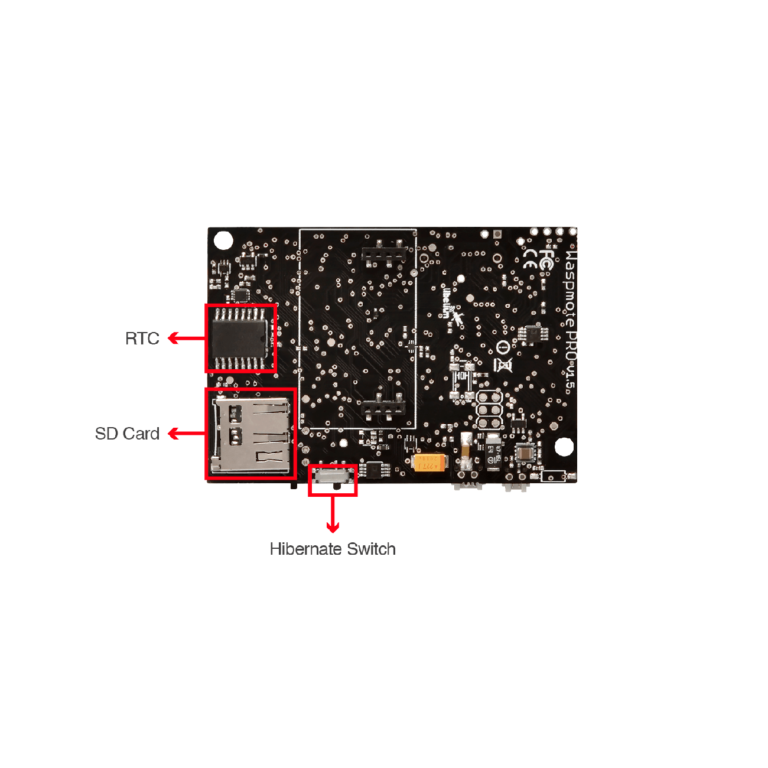
The set of Industrial Protocol modules for Waspmote allows the user to interface with different industrial buses:
1º- Connect any sensor to an existing industrial bus
Waspmote can be configured to work as a node in the network, inserting sensor data into the industrial bus already present. Waspmote can obtain information from more than 70 sensors currently integrated in the platform by using specific sensor boards (e.g: CO, CO2, temperature, humidity, acceleration, pH, IR, luminosity, vibration, etc). This way, the sensor information can be read from any industrial device connected to the bus.
2º- Add wireless connectivity to wired buses
Waspmote can be configured to read the information from the bus and send it to the Libelium IoT Gateway using any of the wireless radio modules available: 802.15.4, 868 MHz, 900 MHz, WiFi, 4G, Sigfox and LoRaWAN.
3º- Connect to the Cloud industrial devices
Waspmote can be configured to read the information coming from the bus and send it via wireless directly to the Cloud using WiFi, GPRS, GPRS+GPS, 3G or 4G radio interfaces.